Recently, "information" is included in the assets of individuals and companies. Information is managed in various forms such as paper media, computer hard disks, and USB memory sticks.
Due to the spread of the Internet, security measures have been sought for these types of information, but what are they?
Various types of computer insecurities, DDoS attacks, ransomware, and other types of computer security threats have become popular.
Still, many cyber-attacks are not as known as attacks on websites. It is crucial for companies that provide online services and those in charge of security measures at the company to develop concrete security measures to familiarize and handle such computer attacks.
Learning from the latest cyber-attack mechanism, more specific actions can be taken, and improved measures can be implemented.
Types of Computer Security
It is vital as a computer user to be aware of the types of computer security and learn how to implement them to avoid common attacks.
The tips below in this article explain the types of computer security. If they are taken into consideration, computer security is almost assured. People in the past and present times have used these tips and greatly benefited from them, especially if you are working remotely or have remote workforce.
1) Protect against Malware
Digital blackmailing attempts by so-called ransomware are critical not only for large networks such as companies, government offices, banks, hospitals, etc. but also for private users - especially if they have not backed up their valuable data.
Malicious software encrypts files and demands a ransom to decrypt them is one of the most common threats. There are also many types of threats that target online banking, games, in-game items, and others that only cause destruction.

Contrary to promises, neither the operating system itself nor "built-in" virus scanners, like the Windows Defender, reliably protect against all types of new malicious codes.
Contrary to promises, neither the operating system itself nor "built-in" virus scanners, like the Windows Defender, reliably protect against all types of new malicious codes.
The primary means of spreading malware are emails with links for special offers, online services that direct users to harmful websites, or ultimately manipulated email attachments, such as alleged applications or invoices.
A good, up-to-date Malware protection product combines sophisticated technologies that can detect malware at several levels and in different places.
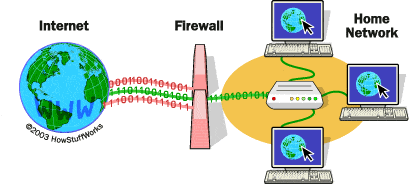
2) Implement Network Segments
Admittedly, Network segmentation sounds complicated.
The idea behind this is that potential attackers only have to find a weak entry point in the Smart TV or the webcam to gain access to all other devices and thus also the stored data.
This is possible if a single router or modem serves them. Attempts to extortion or pure destruction are often the result. This can be curbed by using more than one network or implement Network Segmentation.
This is easier to set up than expected.
One of the steps is to stop the "misuse" of the WLAN.
In this way, all devices that only need Internet access but do not need to access other devices or data can be "disconnected" and placed in a separate network. Thus, criminals can be locked out.
Similarly, network segmentation can be implemented by subnetting and configuring VLAN on routers. Each network is separated from other and hosts are defined based on access requirement. The devices that need access to the local network only can be isolated from the Internet, which can stop harmful internet traffic from reaching them.
Apart from computer security, network segmentation also helps in reducing congestion over the network.
3) Go for a Multi-layered Defense Approach
It is not enough to strengthen the security of terminals on just a single layer, such as what Antivirus Software does.
Multiple forms of computer security sometimes need to be implemented for better protection. If you think about it, a house with only a lock at the entrance, compared to the one with multiple security features such as a lock, surveillance camera, and light enabling sensor, the latter will have a lower risk of an intrusion.
The same applies to corporate network security, where it is necessary to provide multiple layers of defense to reduce the risk of intrusion.
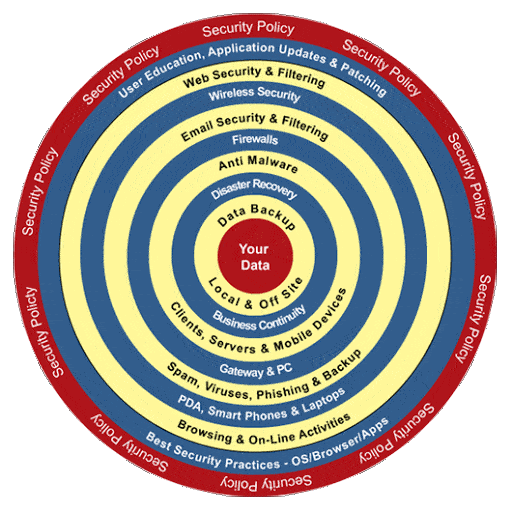
Example of Multi-layered Security Policy
In addition to firewalls, you can implement IPS (Intrusion Prevention System)/IDS (Intrusion Detection System) to detect and prevent unauthorized intrusions and enhance endpoint (desktop computers, laptop computers, tablets, smartphones, etc.) security within an organization.
It is essential to strengthening your protection with the fact that attackers are commercializing for business purposes. Let's make it challenging to get attacked by creating a secure environment that takes time to break in.
4) Apply Access Control
Implementing Access Control is at least as old as working with multiple users on the same system. Most operating systems and other critical applications have started to tie users to basic user access levels and no longer automatically make users with full privileges like administrators.
Administrator or root rights ultimately mean "full access."
If malware gets onto a system, it acts first with the rights of the registered user in most cases. If the user has full access, then the malware also has it. It would first deactivate malware protection and then anchor itself in the system so that it has full access at all times.
By implementing an effective Access Control policy for users, security breaches and human errors can be controlled to a greater extent.
5) Use Firewall
By installing a firewall at the network's entrance/exit (port), you can control the communication such as permitted and denied connection based on the set rules. Such control is called packet filtering. The firewall contains a list of rules which is called an ACL (Access Control List).
Setting a firewall makes it possible to deny or allow network connections by specified sites or software. Therefore, by installing a firewall, you can prevent communication that is not based on defined rules. This means avoiding cyberattacks and preventing users of the organization from communicating in violation of the organization's network usage policy.
For example, P2P file sharing from inside the company can be restricted even if you allow browsing on the Web.
Cyber attacks that use permitted communication rules cannot be prevented, such as IP Spoofing, where the attacker modifies the source address in the packet header that seems legitimate source to the receiving device and the receiver accept it.
It is impossible to deal with security threats only with a firewall, so it is recommended to use it in combination with other methods such as IDS/IPS or WAF (Web Application firewall). This will further enhance the security of your computer and make your data safer.
6) Proper Disposal of Devices
If an electronic device is no longer required, then it makes sense to disconnect it and then dispose of it properly. There are trade-in and take-back programs offered by service providers where you can exchange your old cellphone with a new one, or they simply take it back at a lower price.
Similarly, there are fundraising campaigns where old cellphones, hard drives, USBs, and other electronic devices are recycled for a good cause.
These devices should never end up in regular household waste but should be thrown into special electronic waste bins. These can be found, for example, at the local recycling center or in electronics stores.
In addition to the environmental aspects, users forget that valuable and personal information may still be stored on the devices!
Suppose you pass on the smartphone within the family, for example, to the children. In that case, it is often enough to reset the device to the factory settings. But when the devices that store private and corporate data and information are traded or recycled, the best practice is to use special tools to delete the data or otherwise make it unusable.
Strong industrial magnets from electronics retailers can destroy magnetically stored information. The most effective method is still a good old sledgehammer!
7) Do Better Password Management
Passwords are a security topic that cannot be ignored. Passwords that are easy to guess, reused, or generally too weak and too short, make it easy for cyber-criminals to steal data or manipulate systems.
It's never too late to implement a complex password strategy and avoid using the same password on more than one device. Likewise, avoid using the same password on multiple applications and emails accounts.
There are programs that offer the creation of unique and long passwords encrypted locally and save them via a secure connection in the cloud. Nowadays, password managers can do this reliably and relatively securely.
This way, users can also synchronize the access data between PC / laptop and smartphone using appropriate apps. Although this is not always free of charge, it should be worth the manageable investment.
In addition, more and more online services are offering multi-factor authentication (2FA) or "two-step verification."
The idea behind the principle is that in addition to the user name and password, a second password or a code that is unique for this process is required. These can be generated using individual apps such as Google or Microsoft Authenticator.
The significant advantage of this is that criminals, even though, have the right password in their hands, cannot get into the email, social media, or bank accounts unless they also have the victim's smartphone.
You can also check whether your email address has already become part of data theft through the website, such as "Have I have been Pwned."
In addition to this, always change the default password for the WLAN and the router.
Final Thoughts
Even if we didn't know about advanced computer security challenges and cybersecurity risks during the initial days of computer technology, it was recognized that computer security will always be a critical aspect for workplaces and home users.
The negligence of the basic security measures has made the billion-dollar "cybercrime" market possible in the first place and continues to favor it.
However, as responsible users, we can make criminals' lives difficult and less lucrative because criminals act according to market principles. The higher the effort, the lower the yield, and the more uneconomical the business.
In addition to cybercrime, the "physical" security of data and systems is also crucial. It also depends on the responsibility of the users.
In corporate world, computer security must prevent vulnerabilities and ensure compliance. Computer security is constantly threatened if there is a vulnerability that an attacker can exploit.
IT management should, therefore, identify and close weaknesses or security gaps. Nevertheless, computer security policy must be designed to be as comprehensive as possible to mitigate the risks and provide strict requirements for information and systems.
Computer users, at home or in the office, who have already taken enough security measures just need to keep themselves updated with security advancements and keep their hardware and software updated with the latest versions and security patches.
Business owners who are looking forward to growth need to consider the types of computer security they need to implement. As the data and information is an asset and like any corporate asset, an organization information asset has a financial value that requires security.
It is highly recommended to invest in your company's computer security, in the same way as you invest in other sectors, for your company's growth as weak computer security with loopholes can bring the business down quickly.